In simple terms, SPF, DKIM, and DMARC verify that a sender is authorized to send emails on a website/domain’s behalf. Implementing this authentication shows that you are authorized to send from the domain, and helps to ensure any bad actors are unable to pretend to be you.
Email authentication refers to setting up specific DNS records to prevent emails from being marked as spam, and also increases their deliverability rate. By setting these up, you:
- Improve your open rate;
- Increase engagement with your readers;
- Improve your sender reputation.
SPF, DKIM, and DMARC authentication can be set up by adding TXT and CNAME entries to your server’s DNS records. This is done through your host’s control panel (usually cPanel, Plesk or WHM).
Quick links:
2024 Changes to Sender Domain Authentication
In February 2024, major inbox providers such as Google and Yahoo made their email sender requirements stricter for bulk email senders. This change was aimed at enhancing their ability to effectively block spam, and in turn help protect mail recipients. We have a blog post here with more information about the changes.
The changes apply to all marketers and bulk email senders, and if your campaigns are not compliant, then major mailbox providers may classify them as spam. MailPoet automatically handles some of the changes for you, but there are a few we need your help with to ensure that your marketing campaigns can be delivered successfully.
While setting up domain authentication was recommended in the past, it is now required that all senders set up DKIM and DMARC for their domain.
Please review this section for steps to set up sender domain authentication when using the MailPoet Sending Service.
Common questions
I am not a bulk sender and send very few emails. Do I still need to authenticate my domain?
Yes, to ensure that your email campaigns still reach your audience, it’s a good idea to take action to authenticate your domain if you have not done so yet.
The email industry is trending towards requiring authentication for all senders with the stance of “no authentication – no entry” becoming increasingly popular, and now that the biggest mailbox providers like Google and Yahoo have instated these requirements, we can expect the rest of the industry to follow. Taking action now means that you will be ready for the future, and you won’t get caught by surprise down the line as your business grows (i.e. suddenly having all your emails blocked).
Authenticating your domain when using the MailPoet Sending Service
If you are using the MailPoet Sending Service to send emails, you will need to:
- Set up a branded sender domain, like example.com, rather than sending from a free email address like @gmail.com or @yahoo.com addresses
- Set up DKIM and DMARC authentication by adding the required DNS records via your hosting or domain registrar’s DNS configuration (detailed steps below).
A “sender domain” is the domain you use on your email FROM address. Usually, it is the same domain as your website, but this may not always be the case. If you’re sending your emails as johndoe@example.com, your sender domain is “example.com”.
Note: it’s impossible to set up this authentication for a free email address, such as Gmail.com or Yahoo.com, so you will need to start using a branded sender domain (youremail@example.com). More about it here.
Adding/creating the DNS records
You can start the process of adding your Sender Domain either from your site’s administrator dashboard (described below), or directly in your MailPoet account dashboard here: https://account.mailpoet.com/sender_domains
1. If you need to authenticate your sender domain, you will see a notice in your site’s administrator dashboard asking you to “Authenticate your sender domain to continue sending”

2. You will need to click on the Authenticate domain button and you will see the DNS records that you need to use in order to authenticate your sender domain with DKIM and DMARC.

3. Add the requested DNS records to your domain’s DNS server, and once they have propagated click “Verify DNS records” in the modal (displayed above). You can also verify the domain in your account dashboard here once the DNS records have propagated: https://account.mailpoet.com/sender_domains
Please note that the shop will not automatically keep retrying while waiting for your records to propagate after you add them with your host — you will need to manually click the Authenticate sender domain button to verify the records.

The Manage Sender Domain page may show the following error messages if the DNS records cannot be verified:
- Shows an error message for missing DNS records.
- Displays diffs when DNS records have invalid values.
- Detects and displays diffs when the DNS record host contains a double root domain (
record.test.com.test.com). - Displays errors when the DNS record has multiple values.
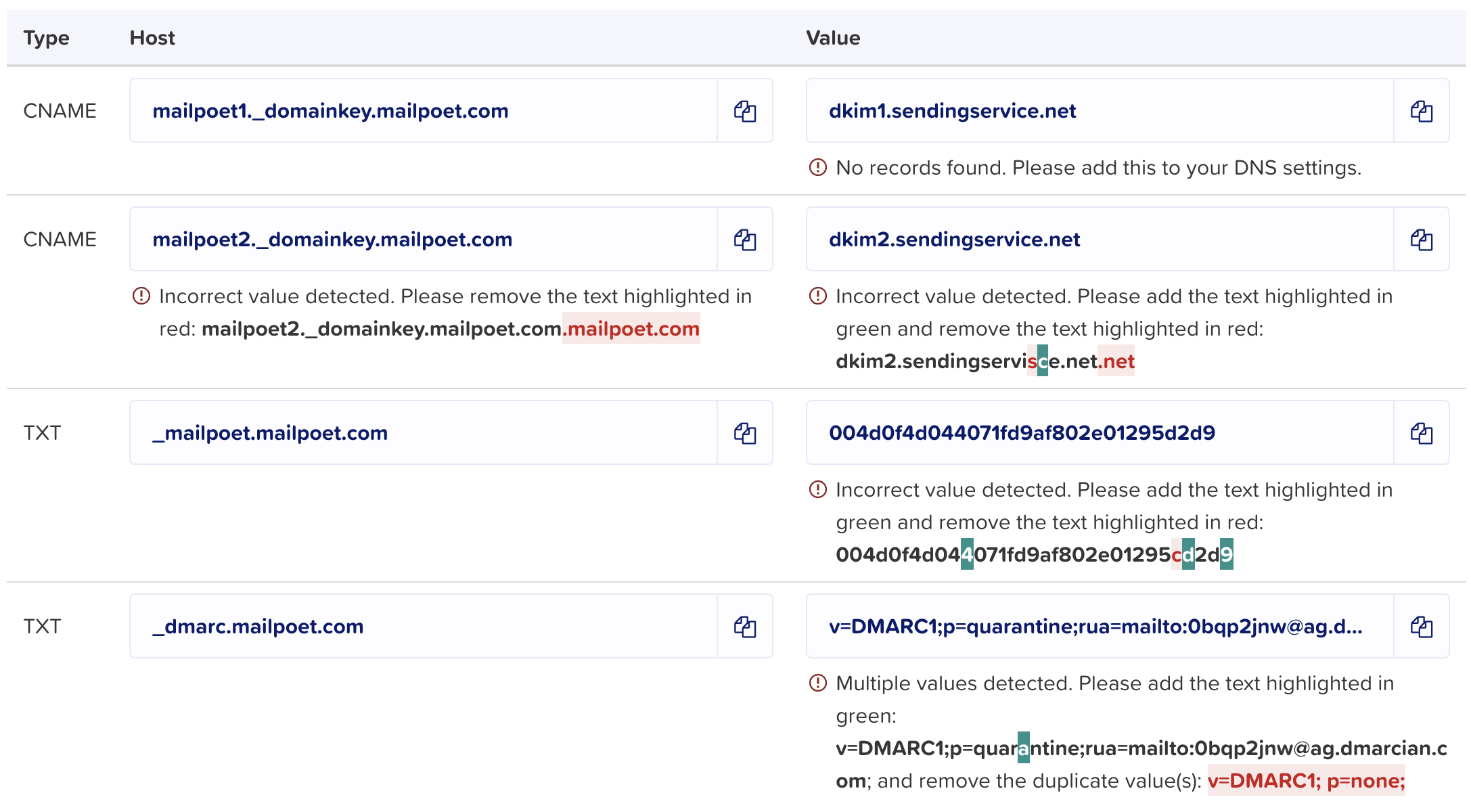
You will need to add the four DNS records through your DNS provider. Usually, it is the same organization you purchased your domain from ( e.g. GoDaddy, NameCheap), or your hosting company.
You need to create two CNAME and two TXT DNS records to set up DKIM and DMARC for your domain properly. The DMARC record’s Value can differ from the default value provided in your account, but it will need to be in valid DMARC syntax.
If you are unsure about adding the records with your host/registrar, please reach out to their support directly as they will need to assist with that.
To make it easier for you, you can check the instructions from some of the most popular hosting providers by referring to the list below:
| Hostinger | cPanel |
| Bluehost | Cloudflare (follow our instructions here) |
| OVH | Dreamhost |
| Ionos | NameCheap |
| Hostgator | GoDaddy |
| DigitalOcean | WordPress.com |
Troubleshooting invalid DKIM records
If you’ve added the records but are having trouble verifying them, you can check if your records are propagated properly and have the correct values in public DNS. To do that, visit these links (change example.com to your sender domain first):
- https://www.whatsmydns.net/#CNAME/mailpoet1._domainkey.example.com
- https://www.whatsmydns.net/#CNAME/mailpoet2._domainkey.example.com
- https://www.whatsmydns.net/#TXT/_mailpoet.example.com
- https://www.whatsmydns.net/#TXT/_dmarc.example.com
If you’ve just added the records, try waiting for 5-10 minutes and then click “Verify DNS records” again. DNS changes can take up to 24 hours to propagate, but often you may see them within 5-30 minutes.
If the records are still showing as “Invalid” in your MailPoet account, please ensure the record types, names, and values in your DNS manager exactly match the ones provided in the MailPoet account dashboard.
If you’re having trouble verifying them, please check if you might be experiencing one of the following cases:
Domain name duplicated
Double-check the DNS record name. Some DNS providers may automatically append the domain to the record, resulting in the domain being duplicated if you also include it when adding the record. For example, if you add a “mailpoet1._domainkey. example.com” record, and the provider appends the domain, that results in it being incorrectly created as “mailpoet1._domainkey.example.com.example.com“. This is the case with GoDaddy and Namecheap, for example.
If this occurred in your case, try removing the domain from the record names, leaving them as ” mailpoet1._domainkey”, “mailpoet2._domainkey”, “_mailpoet”, and “_dmarc” (without the domain, since your host is appending it automatically).
To confirm if this is what’s happening, you can use an online tool like https://www.mail-tester.com/spf-dkim-check — try testing the record with the domain duplicated like in the example above, and check if you find a record for it.
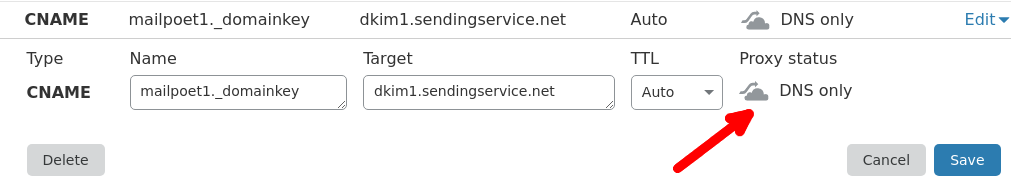
Cloudflare configuration
Proxy status
If you use Cloudflare as your domain’s DNS provider, switch from “Proxied” to “DNS only” Proxy status for both of the CNAME records:
CNAME Flattening
Also, please turn off CNAME Flattening in Cloudflare, as it can cause issues with the DNS resolution and prevent the domain from being verified. More information about CNAME Flattening is available in Cloudflare’s documentation here: https://developers.cloudflare.com/dns/additional-options/cname-flattening/
Email violates Sender Domain’s DMARC Policy

Sending has been paused due to a technical issue with MailPoet: "Error while sending." Email violates Sender Domain's DMARC policy. Please set up sender authentication.
This error happens when you have a DMARC policy set up for your sender domain with a “p=quarantine” or “p=reject” policy, and your sender domain doesn’t have DKIM records pointing to MailPoet. In this situation, your emails sent with MailPoet will be quarantined or rejected. To avoid this, sending is paused on your site until DKIM records are added for your sender domain.
To solve this error, authenticate the sender domain by adding a DKIM record. If you don’t have control over the domain’s DNS settings, please use a different FROM email address. Just make sure it’s authorized on your MailPoet account.
What is SPF?
SPF (Sender Policy Framework) is a DNS record used by your subscribers’ email servers (Gmail, Hotmail, Outlook, self-hosted email, etc.) to verify if your website authorizes the FROM email address you used on your newsletter. This is why you can’t send newsletters with a FROM address using a domain you don’t own. Read our guide on the FROM address.
If you use a third-party service to send your MailPoet newsletters (like SendGrid or ElasticEmail), you’ll need to add their SPF or DKIM records to your website’s DNS. Read how to add or edit your SPF record to help you set up an SPF record in your host’s DNS records.
Users sending with MailPoet’s Sending Service don’t need to set up their own SPF, as messages will automatically have MailPoet Sending Service’s SPF set up. Since you’re sending through our servers, sendingservice.net SPF will be checked, not your domain’s, and it’s expected it’s not aligned with your domain and the sender’s domain. However, as long as DMARC and DKIM records pass, it should not impact your deliverability.
What is DKIM?
DKIM (DomainKeys Identified Mail) is another record added to your host’s DNS records. Your MailPoet install will cryptographically sign your newsletters with a key generated specifically for your domain. When your subscribers receive your newsletter, their email servers will grab the key on your domain’s DNS records. Then, it will use this key to perform a cryptographic authentication to make sure your newsletter was not modified during the sending process.
MailPoet users that send their newsletters using a third-party service, like SendGrid or Elastic Email, already have their messages signed by these services with their DKIM keys. See SendGrid’s document on DKIM and Elastic Email’s guide. If you are sending emails with your own website and want to set up DKIM, please contact your hosting company support to get assistance.
What is DMARC?
DMARC (Domain-based Message Authentication Reporting and Conformance) is an instruction that an email service (e.g. MailPoet) gives to email service providers (e.g. Gmail or Yahoo) about what to do if they receive spoofed emails (like in the case of phishing attacks).
Setting up DMARC for your domain enables you to control and monitor its usage. Malicious actors may impersonate your domain in their spam or phishing emails. Having a restrictive DMARC policy reduces their ability to do so and improves your deliverability at the same time.
Further reading on DMARC records
When setting up your domain as an authorized Sender Domain in your MailPoet account, a default basic DMARC record will be provided that you can use. However, if preferred, you can set up your own custom DMARC record instead, as long as it is valid DMARC syntax. ReturnPath and ProofPoint have great guides on how to set up DMARC.
It will require creating a new DNS TXT Record for a subdomain typically named “_dmarc” to indicate that it is used explicitly for DMARC-related records. For example, if your main domain is “example.com,” the subdomain for your DMARC record would be “_dmarc.example.com”. You can ask your domain provider to help set it up.
If you have never used DMARC for your domain, we recommend starting with a neutral policy (changing the example email addresses to your own):
v=DMARC1; p=none; fo=1; rua=mailto:your-email-address@example.com; ruf=mailto:your-email-address@example.com
Once you ensure that all desirable emails pass DMARC (e.g. after a few weeks of monitoring DMARC reports), you can switch to a more restrictive policy (note the “quarantine” instruction instead of “none”):
v=DMARC1; p=quarantine; fo=1; rua=mailto:your-email-address@example.com; ruf=mailto:your-email-address@example.com
“rua=” specifies addresses where aggregate usage reports should be sent, while “ruf=” specifies addresses that should receive forensic reports.
This will allow you to see who uses your domain to send emails, whether authorized or unauthorized by you.
Tools like Dmarcian can make it easier to collect, process and visualize such reports. If you have a DMARC policy set up for your sender domain with a “p=quarantine” or “p=reject” policy and you are using our MailPoet Sending Service, you need to add DKIM to your sender domain.
How to check your SPF and DKIM keys
You can use this tool to check your SPF and DKIM keys.
Add the website domain where you’re sending your emails from and enter default as your DKIM selector.
You can also run a spam score test if you want to check that they are set up correctly and helping to improve your deliverability.